Standard follows a risk based approach to prioritizing security empha ses and contains practical data control strategies.
Cloud security risk management approach and procedures.
Government of canada cloud security risk management approach and procedures treasury board of canada secretariat cccs itsp 30 031 v2 user authentication guidance for information technology systems.
Each regulated entity should use a risk based approach across key areas listed below to meet fhfa supervisory expectations.
The security related risk can be assessed in a similar structured approach by assessing against selected iso 2700x cobit and nist 800 53 controls that are applicable to the exposures within cloud computing.
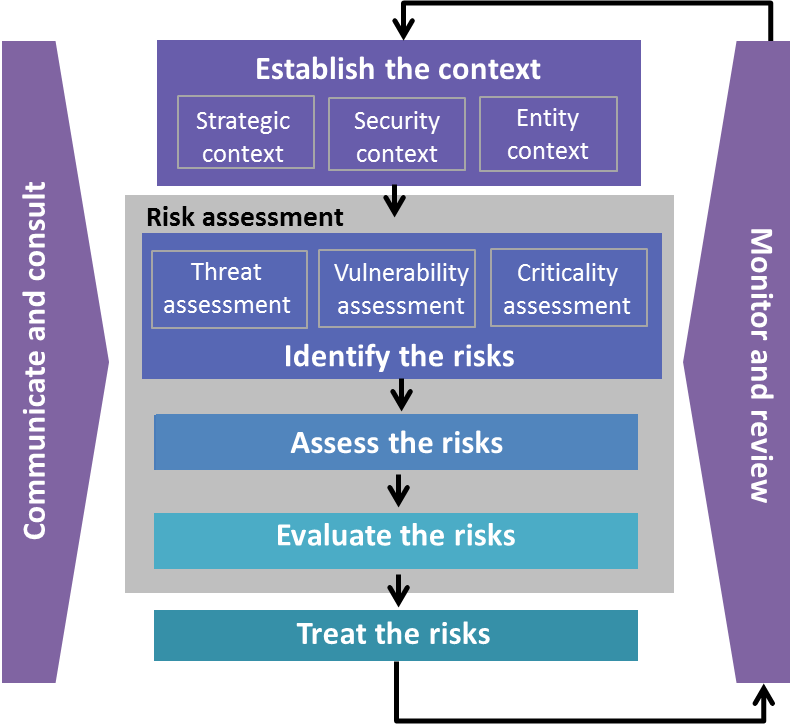
We ll be discussing how gc agencies and departments are cracking down on cloud security in order to handle risks in an effective manner.
The most important classes of cloud specific risks see section 4 risks are.
Help keep your organization secure and compliant with google cloud.
Risk mitigation implementation is the process of executing risk mitigation actions.
Even the government of canada uses cloud service providers on a regular basis.
Management must buy or build management and security in the cloud information risk and security as well as its monitoring and.
And procedures documented approved and implemented.
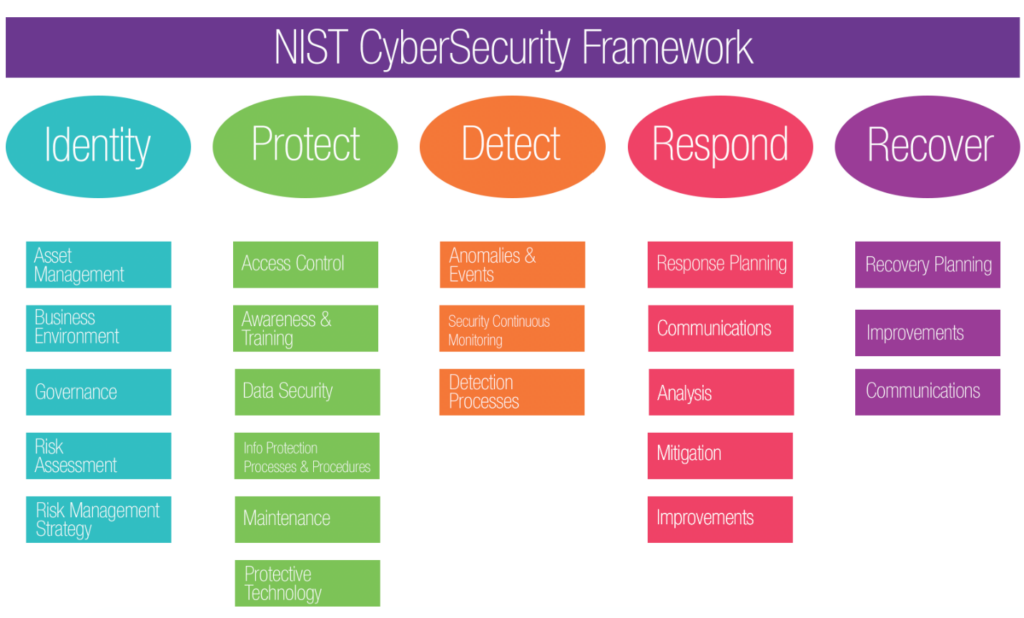
Risk management for cloud computing.
Responsibilities of the board and senior management.
Protect your most valuable data in the cloud and on premises with oracle s security first approach.
Security identity and compliance.
Strategies policies procedures and internal standards.
In addition the standard goes beyond confidentialityand also covers availability and integrity all.
Gc approach to cloud security risk management.
Learn about our privacy and security practices cloud compliance offerings and more.
1 4 top security risks the 2009 cloud risk assessment contains a list of the top security risks related to cloud computing.
Cloud services have become readily available to individuals and organizations.
Oracle cloud infrastructure delivers a more secure cloud to our customers building trust and protecting their most valuable data.
After the first review round the top risks have turned out to be more or less unchanged from the 2009 cloud risk assessment.
Effective risk management of cloud providers is critical to safe and sound operations.
Risk mitigation planning is the process of developing options and actions to enhance opportunities and reduce threats to project objectives 1.
Risk mitigation progress monitoring includes tracking identified risks identifying new risks and evaluating risk process effectiveness throughout the.